State of Solana User Security
Navigating the Intersection of Security and Accessibility: Paving the Way for the Next Billion Users on Solana
“Solana is Scammers favourite chain” or to put it in another way Solana has the largest user traction that scammers are pouring into it.
Introduction
As of now Solana has processed over 270 billion transaction with a market cap of 59 Billion USD. Coming down from a low of $10 dollars to a mark over $135. This has been possible with the convergence of robust infrastructure , thriving ecosystem and thousands of projects that plan to onboard next billion users to Solana.
At current state Solana is the go to chain for anything crypto with a plethora of Dapps that provide best user experience one can have not just in the web3 world but also the web2 world.
Projects like Jupiter , Phantom , Backpack implements the latest security and privacy standards to prevent users from getting scammed at all the levels ranging from protocol level vulnerabilities to client side phishing attacks.
In this report we will dive deep into the client side vulnerabilities and possible optimisations .
What is User/ Client Side Security
Simply said , Everything that a User can interact with needs to secured from attacks.
User or client-side security in the Solana ecosystem refers to the measures taken to protect users and their assets from threats that originate from their own devices or actions. This includes securing private keys, enhancing authentication methods, and implementing safeguards against phishing attacks and other forms of fraud. A user's device, their web browser, and the decentralized applications (dApps) they interact with all play crucial roles in maintaining client-side security.
Why is this important ?
While one may the think that the design of Solana and the overall blockchain is highly secure and immune to attacks but when there is wallet drain , rug pull , key theft like cases. Users feel that their assets are not safe which empirically grows to the state that the blockchain is not safe and finally Solana blockchain is not safe.
Thus handling this small client side security issues at application layer can increase the user experience to an even better level that onboards more users to the ecosystem.
As per the design theory approach , Solana needs to be a consumer facing blockchain that doesn’t mean every second person needs to be a Degen ( crypto expert). We need to assume that user will make mistakes , but our applications Security should be robust enough to protect user assets, even when users make errors, fostering trust and encouraging more participation in the Solana ecosystem.
The Landscape of Attacks Targeting Users
Over 2/3 of all attacks on solana take place by targeting end users. Since the contracts are mostly safe at protocol layer, attackers try to take control of User Wallets in any form possible. Thus if they can’t hack the network they tend to take control from users and this ranges from small targeted dusting attacks to larger seed phrase stealing techniques.
Most of this are development faults and not following the best practises while integrating the frontend services with managed backend or blockchain layer.
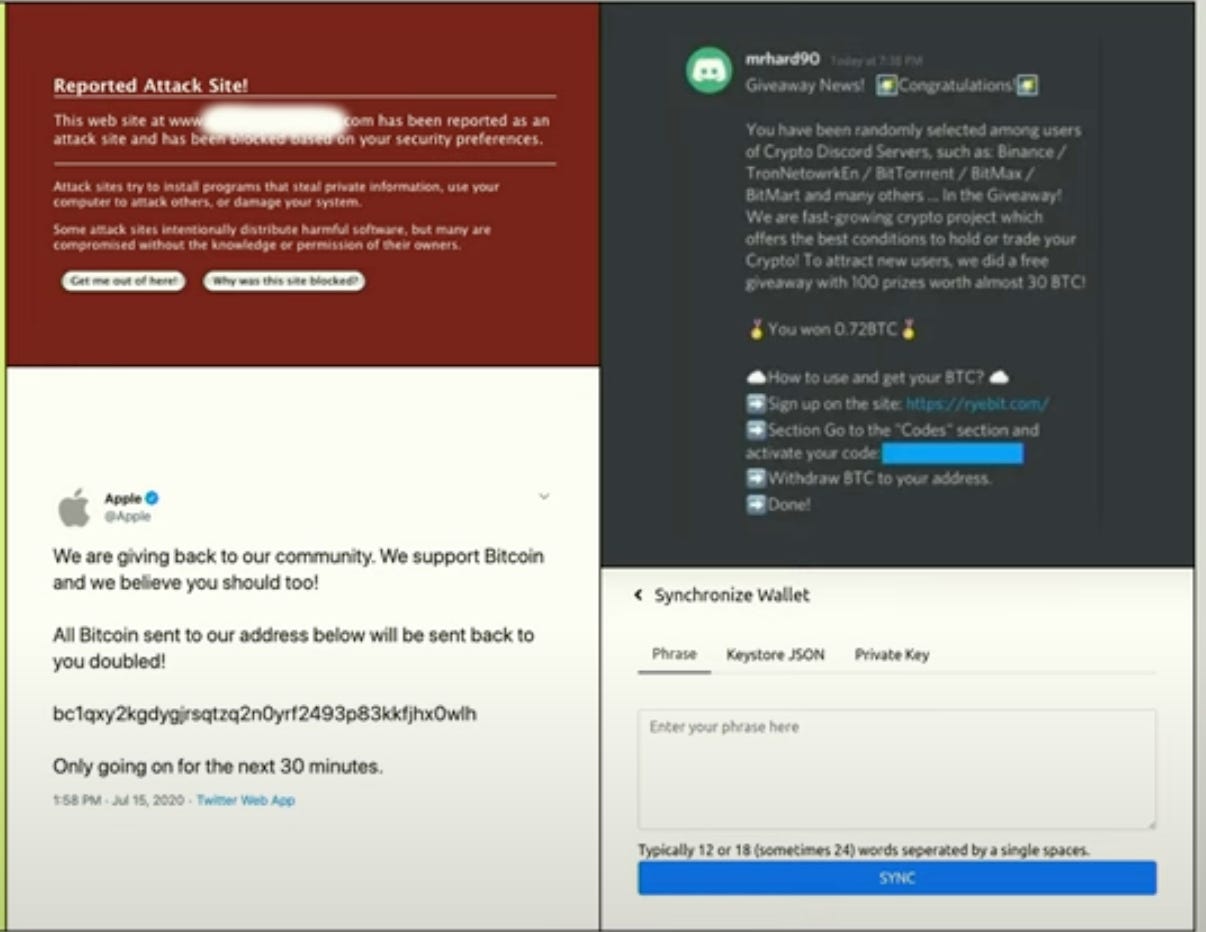
Phishing Attacks in the Solana Ecosystem
Phishing attacks have become increasingly common in the Solana ecosystem. These attacks typically involve scammers impersonating reputable projects or platforms to trick users into revealing sensitive information such as private keys or seed phrases.
Once the attacker has this information, they can take control of the user's wallet and drain it of its assets. It is crucial for users to always verify the authenticity of any communication or website before entering their private information. Implementing additional security measures such as multi-factor authentication can also help protect against these types of attacks.
Some of the popular ways to do them are :
Dusting Attacks
Spam and Scam NFTS
Website Impersonation
Fake and malicious Social Profiles
This mostly happens through sending spam/scam NFTs or zero decimal fungile token ( a fungible token that has just 1 decimal place and generally millions in supply). Attackers love to target users on Solana as compared to other chains solely because of dirt cheap transaction fees and advent of CNFTs that dropped down minting price year on year.
Below we have a short explanation
Dusting Attacks: This is a sophisticated form of attack where attackers send small amounts of tokens (the 'dust') to wallets. These tokens often come with a malicious payload or a tracker that monitors the activity of the wallet. The attackers can then use this information to identify vulnerabilities and launch targeted attacks.
Spam and Scam NFTs: Attackers send unsolicited NFTs to users' wallets. These NFTs may carry malicious code, or they may be part of a scam where the attacker then sends a message to the user, claiming that the NFT is valuable and tricking the user into buying more or paying a fee to 'unlock' a non-existent reward.
Website Impersonation: This is a common type of phishing attack where attackers create websites that look identical to legitimate sites. The goal is to trick users into entering their private keys, passwords, or other sensitive information, which the attacker can then use to take control of their wallets.
Fake and Malicious Social Profiles: Attackers create social media profiles that impersonate legitimate projects or individuals. These profiles are often used to spread false information, scam users into sending funds or revealing private information, or trick users into downloading malicious software.
Identity Verification vs. Exposing Identity
When we engage with airdrop farming platforms, prove our humanity, and complete Know Your Customer (KYC) procedures, we're participating in important practices that allow users and applications to maintain civility and order. But, as beneficial as these practices are, they can also inadvertently expose us to attacks.
Think about it this way. When we sign in to these platforms, our accounts often become exposed to the public. Attackers can exploit this exposure by filtering through Non-Fungible Token (NFT) transactions and prioritizing users based on the balances in their wallets .
Once they've identified high-value targets, they can launch social engineering attacks. These attacks are designed to trick users into revealing sensitive information. They often take place on platforms where users may feel more relaxed and less vigilant, such as Twitter and Discord .
So while these practices offer numerous benefits, they also come with risks. It's crucial that we're aware of these risks and take appropriate precautions to protect ourselves. Here are a few steps we can follow:
Only open verified links provided by trusted wallets such as Phantom and backpack
Always cross-verify Twitter accounts, as many attacks target project's Twitter accounts.
Distribute funds and KYC tasks among different wallets while using tools like assetdash
Use private transfer with Elusiv to interact with cold wallets and Multisig on all major funding accounts.
The Risks of Account Delegation
Account delegation in the Solana ecosystem is a process that allows another wallet or program to have signing rights over a user's assets. In essence, it's similar to granting power of attorney over your funds. This feature is particularly powerful for various use cases such as staking, where a user delegates the management of their stake to a validator.
However, account delegation can be misused by malicious actors to trick users into signing transactions that they did not intend to, thereby gaining control over their assets. Hackers can deceive users into delegating their accounts under the guise of a harmless transaction, and once the delegation is in place, they can drain the user's wallet without their knowledge.
To prevent this from happening, users can utilise tools like Revokin, which provide the functionality to revoke account delegation. The tool allows users to easily inspect their accounts for any delegations and, if found, revoke them with just a few clicks. This is a crucial step in managing your assets on Solana, as it adds an additional layer of security against potential attacks. It's always recommended to regularly check and revoke any unwanted delegations to keep your assets safe.
Take a reference to this :
GitHub - AnishDe12020/solana-delegate-checker
Closing and reopening an ATA that has delegated authority
Follow this best practises with User Flow
Clear communication about delegation transactions: Wallets should explicitly show when a transaction involves delegation of account control. This can be done through specific warnings or notifications.
Use of tools: Tools like Revokin can be very helpful in inspecting accounts for any delegations and revoking them.
Education: Users should be educated about the risks associated with account delegation and the ways to protect themselves from potential attacks.
Strong authentication: Implementing strong authentication methods such as multi-factor authentication can add an additional layer of security.
Improved transaction simulations: Transaction simulations should be enhanced to warn users about potential vulnerabilities they are exposed to.
Problems with SignAllTransactions Method
The SignAllTransactions method, popularly used in Solana dApps, has been identified as a potential security issue. It provides a way for malicious actors to trick users into signing transactions they didn't intend to. It's critical that developers understand the risks involved and implement necessary measures to protect users.
Improving Transaction Simulation Understanding
Source -: Breakpoint 2023: Simulation of Transaction Limitation
Over the course of last three years transaction simulation has improved to be a vital feature in almost all the major crypto wallets. It not only helps users understand what assets are being transferred but also warns them about the potential vulnerabilities they are exposed to.
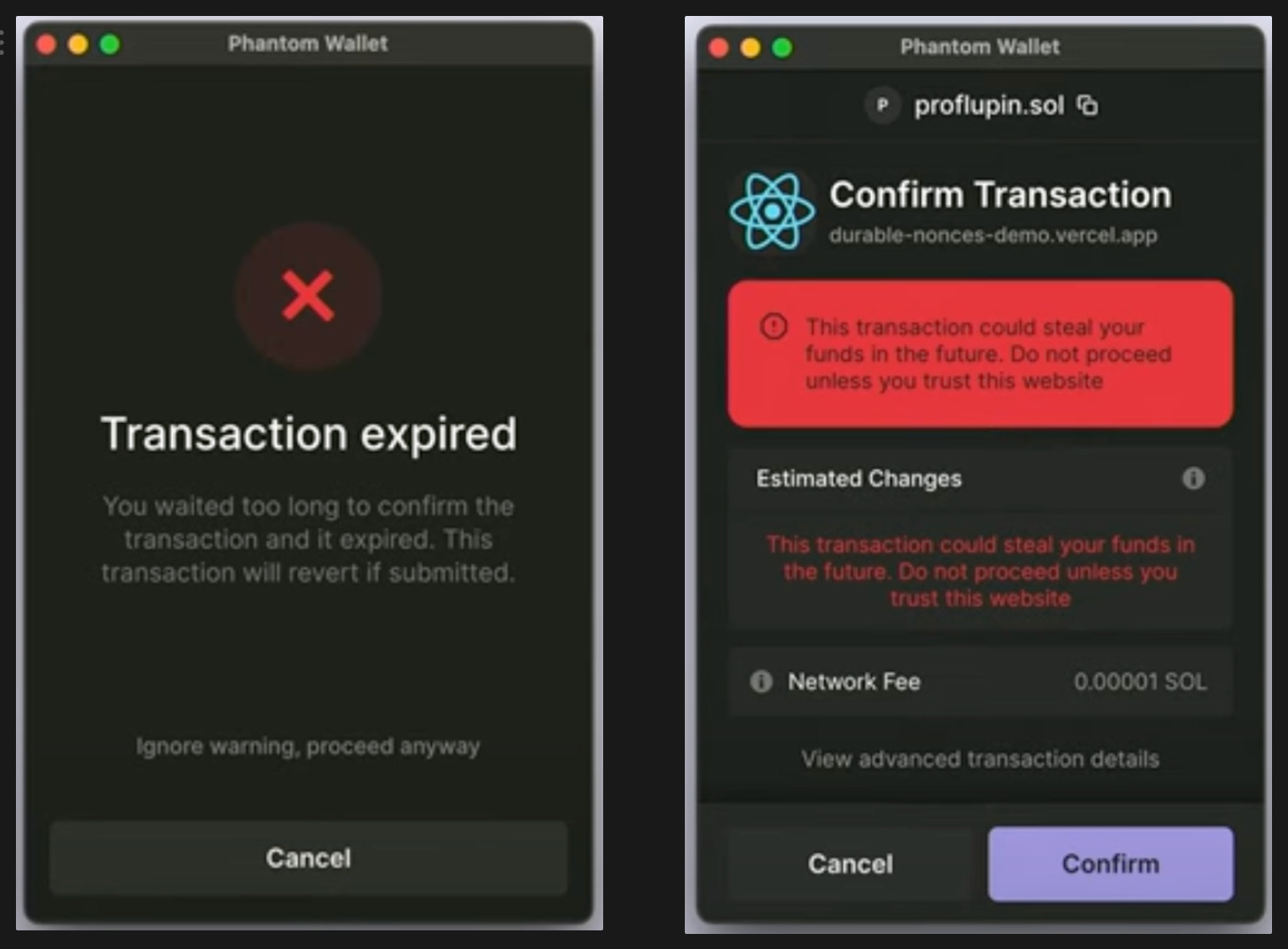
Now transactions on Solana are really interesting , one is to use a blockhash .i.e we haved a forced time of 90 seconds to send a transaction after signing it and so far it is a safer approach .
But things change when we talk about durable nonces , which allows us to submit a transaction any time in future after signing it , an attacker can alter the bits using writeable accounts .
Bad Part : we cant easily predict if transaction is Malicious
Good Part : we can review user that it’s a durable transaction
Also due to the meticulous nature of Solana , Simulation of these transaction is also a centralised thing , almost all the transaction simulation goes through Blowfish Api , making it vulnerable to single point failure .
We already have simulate transaction RPC calls , and for deployment and resolution of the results we need more services like Tinydancer and SPV clients.
Potential Alternatives
We have already deprecated SignandSendTx with SignTx.
But the process to replace SignAllTx with SignAndSendAll transaction is going through solana improvement documents and aims to send each transaction concurrently.
Passkeys and enhanced Authentication Methods
One of the most effective ways to address the issue of key or seed phrase theft in Solana is through the use of passkeys and enhanced authentication methods.
Passkeys are an additional layer of security that users can employ to protect their assets. They work by generating a unique, secure key that is required to access or perform transactions within a user's wallet. This key is separate from the user's seed phrase and can be changed or disabled at any time, giving the user more control over their wallet's security.
By implementing passkeys, the risk of seed phrase theft is significantly reduced. Even if a malicious actor were to gain access to a user's seed phrase, they would be unable to access the wallet or perform transactions without the passkey. This provides an additional barrier that can deter potential attackers.
Enhanced authentication methods like multi-factor authentication (MFA) can also be implemented to further secure a user's wallet. MFA requires the user to provide two or more forms of evidence, or factors, to authenticate their identity. These factors could include something the user knows (like a password or passkey), something the user has (like a smart card or mobile device), or something the user is (like a biometric verification such as a fingerprint or face recognition).
Implementing MFA can provide a robust security solution that can prevent unauthorized access to a user's wallet. Even if an attacker is able to acquire a user's seed phrase or passkey, they would be unable to access the wallet without the second factor of authentication.
By implementing these security measures, Solana can address the issue of seed phrase theft and provide users with more control over the security of their assets.
Also check : https://github.com/Bunkr-2FA/secp256r1-verify-instruction
Lighthouse - The Assertion Solana Program
https://github.com/Jac0xb/lighthouse
Lighthouse is a Solana program designed to provide assertion instructions that can be appended
to transactions. If a malicious actor attempts to spoof simulation results, overspend during the transaction, or put an oracle account into an undesirable state, the assertion with Lighthouse will fail, thus causing the transaction to fail.
This tool is designed to be simple and allows users to append assertion instructions to existing transactions without the need to write new Solana programs. It is an open-source, public utility Solana program that places emphasis on security, composability, and community involvement.
Lighthouse can be utilized in various scenarios such as checking account state before allowing data to be mutated. It can also be used as a guardrail during a transaction, by appending a Lighthouse assertion instruction to the transaction which states that a specific account balance must be a certain amount at the end of the transaction. If the balance does not match the specified amount, the transaction fails.
This tool is extremely useful in the Solana ecosystem, as it allows users to make assertions about on-chain state and instruction-level delta of these state changes without the need to deploy additional Solana programs.
Balancing Security with User Experience
The user experience on Solana's platform is unparalleled, largely due to the seamless interaction and efficient transactions facilitated by various exchanges and asset management platforms. For instance, Jupiter, a renowned exchange on Solana, offers a user-friendly interface and a wide variety of trading options, making it easy for both beginners and experienced traders to navigate the crypto market.
Additionally, Squad's multisig wallet adds another layer to the exceptional user experience by providing a secure and convenient way to manage assets. This wallet allows multiple users to hold the keys to a single wallet, enhancing security and promoting collective decision-making.
Other platforms like Serum DEX, Radium, and Mango Markets also contribute to the superior user experience by offering advanced trading features, easy staking options, and efficient lending and borrowing services. All these features, combined with Solana's high-speed and low-cost transactions, make the user experience truly remarkable.
Future Directions in Solana Security
In conclusion, the Solana ecosystem is in a robust position, offering the best user experience in the web3 space. We are consistently onboarding new users, which is a testament to the strength and appeal of our platform.
However, we recognize that user retention has been affected by unfortunate incidents. We are committed to improving this by bolstering our security measures and continuously refining our systems.
This commitment to user safety, along with our dedication to maintaining a superior user experience, ensures that user will remain and have a hassle free experience even without spending funds on hardware wallets.